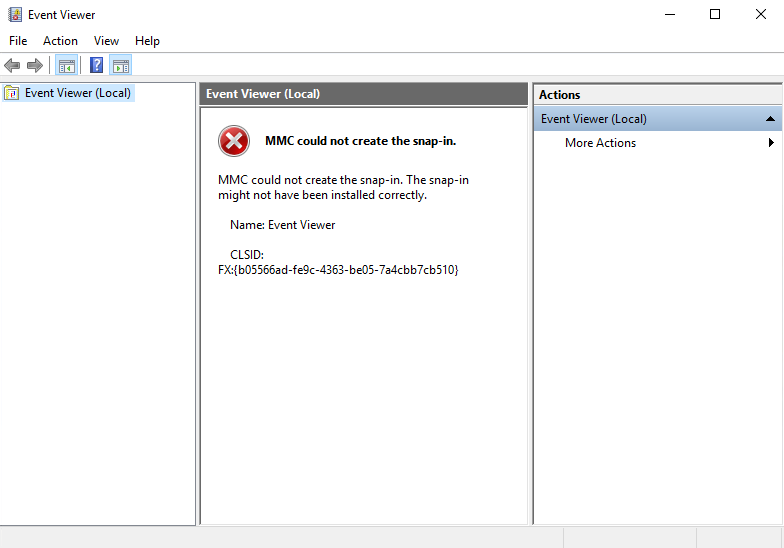
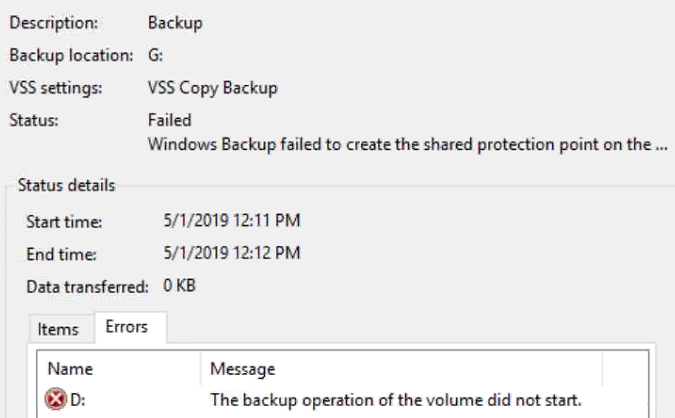
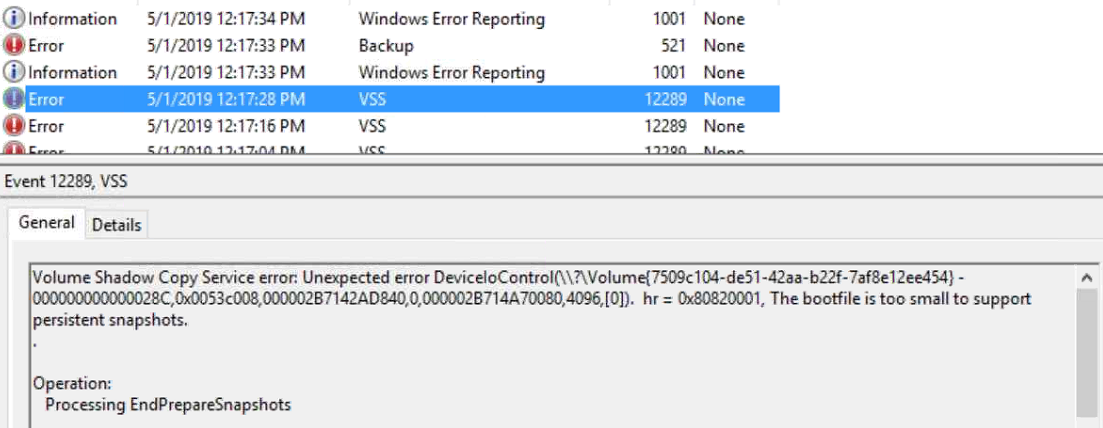
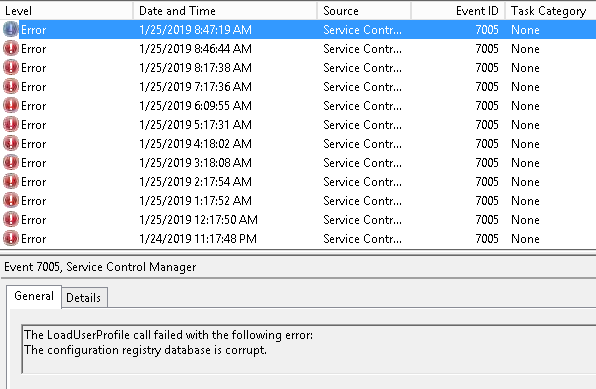
Good morning. I wanted to document an issue I have seen several times. The fix for this problem is pretty easy in PowerShell, but would take quite a bit of time using Server Manager. The reason for the wizard is failing at 16% is due to the inability to connect to a domain controller in the domain. This failure to connect is due to none of the roles being installed and therefore the server not being promoted to a domain controller. This can all be discovered from the Essentials deployment logs in the C:\ProgramData\Microsoft\WindowsServer\Logs folder.
As I stated above the fix is pretty easy. Run the three PowerShell commands below, changing domainname to the name you want for your domain and the P@ssW0rD! to a password of your choosing. Keep in mind this password must meet complexity requirements with a length of at least 8 characters and 3 of 4 character types; capital letter, lowercase letter, number, special character.
NOTE: If you do not want the default computer name of WIN-<random string>, then you should change the computer name via the sysdm.cpl application or use netdom.
Also, change domainname.local to a domain name of your choice that ends in .local. For instance tailspintoys.local or contoso.local. You will not be able to change the computer or domain name after completing the wizard.
Install-WindowsFeature AD-Domain-Services,DNS,FileAndStorage-Services,File-Services,FS-FileServer,FS-BranchCache,FS-DFS-Namespace,Storage-Services,NPAS,RemoteAccess,DirectAccess-VPN,Remote-Desktop-Services,RDS-Gateway,Web-Server,Web-WebServer,Web-Common-Http,Web-Default-Doc,Web-Dir-Browsing,Web-Http-Errors,Web-Static-Content,Web-Http-Redirect,Web-Health,Web-Http-Logging,Web-Log-Libraries,Web-Request-Monitor,Web-Http-Tracing,Web-Performance,Web-Stat-Compression,Web-Security,Web-Filtering,Web-Basic-Auth,Web-Client-Auth,Web-IP-Security,Web-Windows-Auth,Web-App-Dev,Web-Net-Ext45,Web-ASP,Web-Asp-Net45,Web-ISAPI-Ext,Web-ISAPI-Filter,Web-Includes,Web-Mgmt-Tools,Web-Mgmt-Console,Web-Mgmt-Compat,Web-Metabase,Web-Scripting-Tools,ServerEssentialsRole,NET-Framework-45-Features,NET-Framework-45-Core,NET-Framework-45-ASPNET,NET-WCF-Services45,NET-WCF-HTTP-Activation45,NET-WCF-TCP-PortSharing45,BranchCache,GPMC,RSAT,RSAT-Role-Tools,RSAT-AD-Tools,RSAT-AD-PowerShell,RSAT-ADDS,RSAT-AD-AdminCenter,RSAT-ADDS-Tools,RSAT-ADCS,RSAT-ADCS-Mgmt,RSAT-DNS-Server,RSAT-NPAS,RSAT-RemoteAccess,RSAT-RemoteAccess-PowerShell,RPC-over-HTTP-Proxy,FS-SMB1,Windows-Defender-Features,Windows-Defender,Windows-Defender-Gui,Windows-Internal-Database,WAS,WAS-Process-Model,WAS-Config-APIs,Search-Service,Windows-Server-Backup,WoW64-Support
$Password = ConvertTo-SecureString “P@ssW0rD!” -AsPlainText -Force
Install-ADDSForest -DomainName “domainname.local” -SafeModeAdministratorPassword $Password -Force
After the above commands complete the server will automatically restart and the deployment wizard should complete without further errors. If it is failed, then click Retry. I have seen a few instances where a retry is necessary.
I hope you found this post helpful. If you have anything to add, please do so in the comment section below.